There are many tools for port scanning. One of the tools is the same tools I posted on my previous blog entry, hping3. While hping3 is a very powerful tools to do a penetration testing, this week I will explore other tools, UnicornScan. UnicornScan is a built-in tools in Kali Linux. But if the tools is not there yet, you can use this command :
sudo apt-get install UnicornScan
This is a normal scan using UnicornScan :
Notice I used -B 445 in my Command Line. -B is to determine the source port of the packet. In this Case the packet is originated from port 445. I was targeting my Windows XP machine. As you can see my Windows XP have some port opened. It's the http, epmap, netbios-ssn, https, microsoft-ds.
This is the wireshark record in my Windows XP target machine :
See the record number 48 and 49. My Kali Linux (172.16.1.130) sent TCP SYN Packet to my Windows XP (172.16.1.128). Maybe you can't see the packet detail in this screenshot (Kinda My Fault, Sorry) but the specific port it targeting is port 80 (http port). The port is opened so the Windows XP sent back the TCP SYN,ACK Packet to my Kali Linux.
The Protocol used is TCP, but UnicornScan can also use another protocol mode by using --mode command line. There are several mode to be used such as --mode U for UDP, --A for ARP.
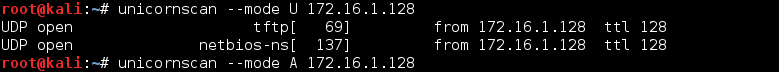
This is the Screen Shot of UnicornScan in UDP mode :
This is the result of UDP port scan. It will return the result of open UDP port such as tftp, and netbios-ns.
There are also sniff mode. Like this :
There are so many information in sniff mode. I'm sorry I myself still can't explain all of the information but I'll promise I'll learn about it and post the explanation once I fully understand.
There are some issues if you use the same source port again and again. In this case I used port 445 as source port again and again. This is the result in the target machine's wireshark :
You can see in the wireshark are specified that there are a lot of port reuse (port 445)
Before I forget, UnicornScan can also spoof your IP address by using --source-addr (IP).
In my devious picture I spoofed my IP to 250.250.250.250.
That's all for this week. I hope this will help you all.




Tidak ada komentar:
Posting Komentar