First of all, what is social engineering ? Social engineering is art of deception to harvest information from human vector or exploiting human weakness in order to gain information. In hacking cycle, social engineering is an optional step. It means it is not necessary to be done in order to hack into a system. Even though it is optional, social engineering holds a very important aspect which allow the hacker to gain an easier way to hack or when all step in hacking cycle fails, social engineering might be the last option in order to hack the system.
There are top 5 social engineering exploit that can be used :
1) Familiarity Exploit - Making yourself familiar to those you want to exploit and lower their guard. In a world of psychology, people react differently to other people according how close those people are. You can make yourself closer to your target by making yourself familiar to the target such as increasing the number of encounter, getting same interest and the most important thing is to not create a mindset of "Who is that and why is he here ?".
2) Creating a Hostile Situation - What it means by hostile situation is to create a situation which the atmosphere is tense such as angriness. This situation can be easily created or faked by a simple technique like when you have a phone cal with your target you fake a tense fight with someone else while still on the phone. By basic psychology, people will not like an angriness and will try to get rid of it, so people tends to follow your order when you are mad. Use this chance to exploit your target
3) Gathering and Using Information - Gather info as much as possible of your target. The more info you have about your target, the more possibilities that your social engineering to works. There are a lot of ways to gather information such as : Online site ( Facebook, Linked in, etc ), The target work place, asking target's friends or colleague.
4) Get a Job at your Target Workplace - If the payment of the penetration job is worth it, just get a job there. Most small to medium sized company will not do any background check on you, so you can easily get a job there without being afraid of your identity being compromised. Once inside, you can climb your way to earn their trust so you can get access to sensitive information. Once you get the information it wont'be hard for you to exploit it.
5) Reading Body Language - To be able to read a body language, you may need an advanced knowledge in psychology. But it is worth it. The basic explanation is to make your target comfortable as much as possible. When people get comfortable they will be talk more easily and they will feel more eager to help you without questioning your motives. By making them comfortable, you can basically exploit information from them.
According to this technique, someday maybe you can be the initiator of the social engineering or maybe you can be the target of social engineering. With this in mind, be careful about what information you share and do not give any information to people that is not authorised to know those information.
Johny Blog
Minggu, 08 Juni 2014
Threat of SQL Injection
What is SQL injection ? SQL Injection is a code injection technique, used to attack data-driven application. in which malicious SQL statements are inserted into an entry field for execution. According to Open Web Application Security Project (OWASP) SQL injection is rated to be the top threat to web application.
By using SQL injection technique, a hacker can easily enumerate the target database to gain sensitive information such as username, password, etc. SQL injection is not always successful. Not all website is vulnerable to SQL injection. Some website with input validation in their form will not be easily injectable.
An SQL injectable website will result in following pages (or similar) when you input " ' " (Single Quotation Mark). This is the example of SQL injection vulnerable website :
By using SQL injection technique, a hacker can easily enumerate the target database to gain sensitive information such as username, password, etc. SQL injection is not always successful. Not all website is vulnerable to SQL injection. Some website with input validation in their form will not be easily injectable.
An SQL injectable website will result in following pages (or similar) when you input " ' " (Single Quotation Mark). This is the example of SQL injection vulnerable website :
This website do not have input validation in their log in form so when a " ' " (Single Quotation Mark) is inputed, the code will consider this input to be an SQL query which result in the above error page.
This means the hacker can exploit the database and in worst case scenario the hacker can take the ownership of the website.
With this SQL injection threat, it is highly encouraged for web developer to develop a web site with SQL injection defines such as :
- Input Validation in Log in Form
- Use Web Application Firewall
- Limit Database Privileges
Selasa, 20 Mei 2014
Phishing Attack Using SETOOLKIT
Phishing an attack that intended to acquire private information such as user name, password, credit card detail, etc. The most common way of phishing attack is make a "fake" site that require you to login to those "fake" site. After you login, your input such as user name and password will be recorded or key logged by the hacker.
This time I will explain how to make "fake" website using setoolkit. In Kali Linux, setoolkit is already installed so to run it just open the terminal and type setoolkit. In case you can't run it, use
su - root first to attain root privilege.
This is the main menu of :
Input 1 and hit enter to select Social-Engineering Attack :
Input 2 and hit enter to select Website Attack Vector, after that input 2 and hit enter again to select the harvester attack. After that you will be prompted to enter the host IP address for the "fake" website. In this image below, I inputed my Kali Linux IP 192.168.5.131. Hit enter again and you will be prompted to input the URL of the "real" link to be cloned by setoolkit and the view will be like below image. YOU HAVE TO KEEP THIS TERMINAL RUNNING AND DON'T STOP THE SETOOLKIT :
Now open the "fake" page in other VM (I used my XP) and it will just like real Facebook login page:
Note the IP is my Kali Linux IP and not the real URL Facebook.com. Next i tried to input random user name and password. I used test@test.com for username and testiest for password :
And when I submitted the user name and password this is what will happen in setoolkit terminal :
Every input is recorded by the terminal. The user name and password is perfectly key logged.
So with this in mind I will advice you to be careful when you get an e-mail that redirect you to such website and prompt you to log in. Please check the URL of the website first and DO NOT OPEN LINK PROVIDED BY UNKNOWN SENDER !
Selasa, 13 Mei 2014
How to Know Open, Closed, Filtered Port from Wireshark Packet Capture
In port scanning there are 3 port status, open, closed, filtered port.
Open port means the port is open and running a service for the machine.
Closed port means the port is close and not running any services.
Filtered port means that your probe to these specific port is filtered or dropped by the firewall.
For this test, I used mmap -F 172.16.128 command to scan fewer port to only show you guys the result in wireshark.
This is the result of closed port in wireshark :
As you can see, there are many SYN request to the target port and the target port immediately reply with RST,ACK. From this result we know that the port is closed.
This is the result of open port in wireshark :
From this wireshark packet capture, you can see at packet number 63 sent a SYN packet to http port of the target. At Packet number 65, the target http port sent a SYN,ACK reply which means the port is open and running a service.
And this is the result of filtered port in wireshark :
There is no reply at all from the target machine. This means the probe packet we sent is not even reach the target port because the packet is dropped by the firewall.
Zenmap, GUI version of NMAP
Zenmap is an NMAP with Graphical User Interface(GUI) support for easier use. To execute Zenmap in Kali Linux it is very simple. It is recommended to run Zenmap by using root privileges or some NMAP scan will not be available.
This will pop-up if you're not running Zenmap using root privileges :
And this is the fully running Zenmap will look like :
Notice in this Picture, I used my windows XP Virtual Machine(172.16.1.128) as the target. And we can select a scan profile. This scan profile will provide us with NMAP scan command. Here are some of the Scan Profile :
Intense Scan
-T4 : Scan Timing Mode 4 (See Description Below)
-A : Enable OS detection, Version Detection, Script Scanning, and traceroute
-v : Verbose mode, it will give detailed info of what the mmap is currently doing
Intense Scan with all TCP port scanned
-p 1-65535 : Scan the port range from port 1 to 65535
-T4 : Scan Timing Mode 4 (See Description Below)
-A : Enable OS detection, Version Detection, Script Scanning, and traceroute
-v : Verbose mode, it will give detailed info of what the mmap is currently doing
Quick scan
-T4 : Scan Timing Mode 4 (See Description Below)
-F : Fast Mode, will scan fewer port than the regular scan
If you notice, all of the scan above use -T4 which is Timing Mode 4. You can use from -T0 to -T5 (but only one at a time), and here are the description:
-T0 : Paranoid Scan
-T1 : Sneaky Scan,
-T2 : Polite Scan
This Scan will slow down the scan to use less bandwidth and target machine resources. This modes is used in IDS evasion.
-T3 : Normal Scan
This is the default scan used by NMAP if the timing mode is not declared in the command.
-T4 : Aggressive Scan
This Scan will speed up the scan with assumption that you are in a reliable network
-T5 : Insane Scan
This mode will scan with assumption that you are on a extremely fast network and willing to sacrifice accuracy for speed
Kamis, 10 April 2014
WireShark "TCP Port Number Reused" Entry
For the continuation of my previous blog entry, I will explain about "TCP Port Number Reused" entry in my wireshark data record.
The simplest explanation would be there are so many same TCP SYN Packet from the same IP address with same port which already been captured by the wireshark before.
The more technical explanation is because in port scanning, my Kali Linux sent a lot of packet to the windows XP and it keeps trying to open new port every time.Wireshark does not simply forget the source address and port it has seen or captured before. Because I used port 445 alot from the same IP (250.250.250.250 in last picture.) Wireshark display the TCP Port Number Reused because wireshark captured the similar connection source before (In relatively short time). It won't Display this entry if the same connection isn't happened in relatively short time.
The simplest explanation would be there are so many same TCP SYN Packet from the same IP address with same port which already been captured by the wireshark before.
The more technical explanation is because in port scanning, my Kali Linux sent a lot of packet to the windows XP and it keeps trying to open new port every time.Wireshark does not simply forget the source address and port it has seen or captured before. Because I used port 445 alot from the same IP (250.250.250.250 in last picture.) Wireshark display the TCP Port Number Reused because wireshark captured the similar connection source before (In relatively short time). It won't Display this entry if the same connection isn't happened in relatively short time.
Port Scanning
Port Scanning is a very important step in Hacking and Penetration Testing. Port Scanning is used to find which port is vulnerable in the target system to be exploited. We need to find vulnerable port because in the end, we need an open unfiltered port to send packet to the target system. Open port is not always exploitable. Open port may be filtered. A filtered port is an open port that are guarded by the firewall.
There are many tools for port scanning. One of the tools is the same tools I posted on my previous blog entry, hping3. While hping3 is a very powerful tools to do a penetration testing, this week I will explore other tools, UnicornScan. UnicornScan is a built-in tools in Kali Linux. But if the tools is not there yet, you can use this command :
There are many tools for port scanning. One of the tools is the same tools I posted on my previous blog entry, hping3. While hping3 is a very powerful tools to do a penetration testing, this week I will explore other tools, UnicornScan. UnicornScan is a built-in tools in Kali Linux. But if the tools is not there yet, you can use this command :
sudo apt-get install UnicornScan
This is a normal scan using UnicornScan :
Notice I used -B 445 in my Command Line. -B is to determine the source port of the packet. In this Case the packet is originated from port 445. I was targeting my Windows XP machine. As you can see my Windows XP have some port opened. It's the http, epmap, netbios-ssn, https, microsoft-ds.
This is the wireshark record in my Windows XP target machine :
See the record number 48 and 49. My Kali Linux (172.16.1.130) sent TCP SYN Packet to my Windows XP (172.16.1.128). Maybe you can't see the packet detail in this screenshot (Kinda My Fault, Sorry) but the specific port it targeting is port 80 (http port). The port is opened so the Windows XP sent back the TCP SYN,ACK Packet to my Kali Linux.
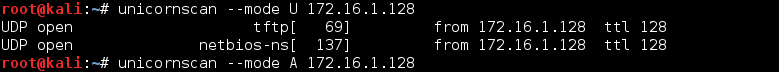
The Protocol used is TCP, but UnicornScan can also use another protocol mode by using --mode command line. There are several mode to be used such as --mode U for UDP, --A for ARP.
This is the Screen Shot of UnicornScan in UDP mode :
This is the result of UDP port scan. It will return the result of open UDP port such as tftp, and netbios-ns.
There are also sniff mode. Like this :
There are so many information in sniff mode. I'm sorry I myself still can't explain all of the information but I'll promise I'll learn about it and post the explanation once I fully understand.
There are some issues if you use the same source port again and again. In this case I used port 445 as source port again and again. This is the result in the target machine's wireshark :
You can see in the wireshark are specified that there are a lot of port reuse (port 445)
Before I forget, UnicornScan can also spoof your IP address by using --source-addr (IP).
In my devious picture I spoofed my IP to 250.250.250.250.
That's all for this week. I hope this will help you all.
Langganan:
Komentar (Atom)